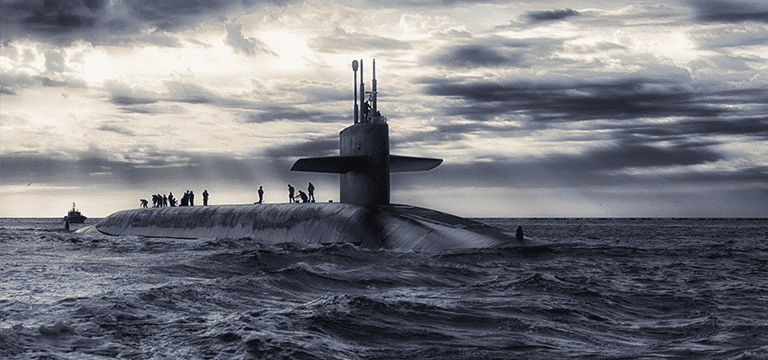
Serving aboard a nuclear-powered, fast-attack submarine in the early 90s, we once conducted naval war games with surface fleets of several nations off the coast of Portugal. On one operation, our mission was to hunt and “destroy” an aircraft carrier (a rather large target), while avoiding anti-submarine warfare (ASW) tactics deployed by “enemy” aircraft and other surface vessels tasked with finding us and protecting the “mother ship”. After several hours of a series of evasive and well-executed maneuvers conducted by our highly skilled captain, we were able to position ourselves close enough to the carrier to launch a flare (out of a 3” launch tube) onto the deck of the massive ship signifying that we had accomplished our goal. I recall there seemed to be something rather gratifying in bringing down such a large target – even if pretend.
Speaking of large targets, it’s no mystery that the healthcare industry is the target of many nefarious groups bent on exploiting healthcare organization’s weaknesses and having their way with them. While their main goal may not be to sink the organization per se, they certainly go a long way toward accomplishing that with the havoc they create. According to Becker’s Hospital Review, more than 27 million patient records were breached in 2016. Of those, hacking and ransomware alone were responsible for well over 7 million. Both Becker’s and Health Data Management confirmed that Providers were among top targets for cyber attacks in 2016.
Beside testing military skills and tactics, an important aspect of playing wargames is to identify potential weaknesses that can be exploited, learn from that information, and then implement measures moving forward that will help avoid risk of loss, thus making the ship a stronger force to contend with. We mentioned doing a risk assessment in a prior article, but as HealthITSecurity.com points out, “healthcare risk assessments are not only required under HIPAA regulations, but can also be a key tool for organizations as they develop stronger data security measures.” The goal is to ensure that Protected Health Information (PHI) stays secure. Risk assessments are one way to mitigate risk.
Training, training, training. The submarine days were filled with it. Training and re-training on specialized equipment. Battle stations training at shore-based simulator schools. We even conducted training exercises whereby we would simulate being underway while remaining tied to the pier. Training is the second way to mitigate risk. The basic concept behind training is that doing the right thing should be automatic. Doing the correct actions should be behaviors we shouldn’t need to think a whole lot about, and training helps ensure this is possible. We’ve mentioned this article before regarding guidance on setting up a training program, but outside resources such as HIPAATraining.com may be an investment worth looking into. This website has a HIPAA Security Training course available for $30 per individual which, among other things, covers safeguards required to protect the security of protected health information in electronic form. Security awareness solutions may be another avenue in helping to adequately train staff to further protect your organization from hackers and ransomware.
The third way to mitigate risk is through encryption. I can’t speak regarding submarine communication activity and data security measures as it was mostly outside my job responsibility. However, one shouldn’t have to reach too far to consider that for a submarine to retain its tactical advantage, its communication and data must remain secure. Trend Micro reveals that not only is the Healthcare industry the most frequent victim of data breach crimes, both Personally Identifiable Information (PII) and Healthcare data (because it contains PII) are the most popular record types stolen. Dataencryption is a tactical defense every healthcare organization should employ in managing electronic protected health information (ePHI). Encoding the text of these sensitive records is an important step in the direction of mitigating risk. As a leading release of information company, ChartRequest uses industry-leading data protection and military-grade security policies combined with full 256-bit SSL encryption, 2048-bit private keys, and AES multi-layered encryption for all documents and data, both at rest and in transit. In fact, we force the https:// standard for all desktop, mobile, web and API communication features, protecting from unauthorized access over wireless and wired networks.
Unfortunately, healthcare organizations are the big ship that can’t be missed in the middle of the ocean of organizations, and they are being targeted by criminals who work hard to compromise ePHI. Let the 27 million breached records in 2016 serve as a flare warning on the deck to let us all know, we’ve got to do what it takes to mitigate risk for our respective organizations. The three areas – identifying weaknesses through risk assessment, consistent training, and data encryption will go a long way in winning the war against Healthcare data breach!