Leading Medical Records Retrieval Solution with a Risk-Free Consultation!











Secure
HIPAA Compliant
Top-Rated
Get Records You Need When You Need Them
Healthcare Providers
Our release of information solution is purpose-built to streamline the exchange of PHI, reduce status update phone calls, access powerful reports, and so much more. Keep the process in-house, or let our experts release records for you.
- Support referral management and care coordination,
- Prevent Right of Access and information blocking issues,
- Minimize the risk of human error with an easy-to-use workflow.
Lawyers and Attorneys
Tired of constantly calling for status updates when you need a client’s medical records? Automate the follow-up and easily beat court deadlines by letting our experts chase records for you with CaseBinder.
CaseBinder helps lawyers and attorneys:
- Submit record requests quickly on our easy-to-use platform,
- Access status updates 24/7 while our team works on retrieval,
- Save on retrieval costs for every request we process.

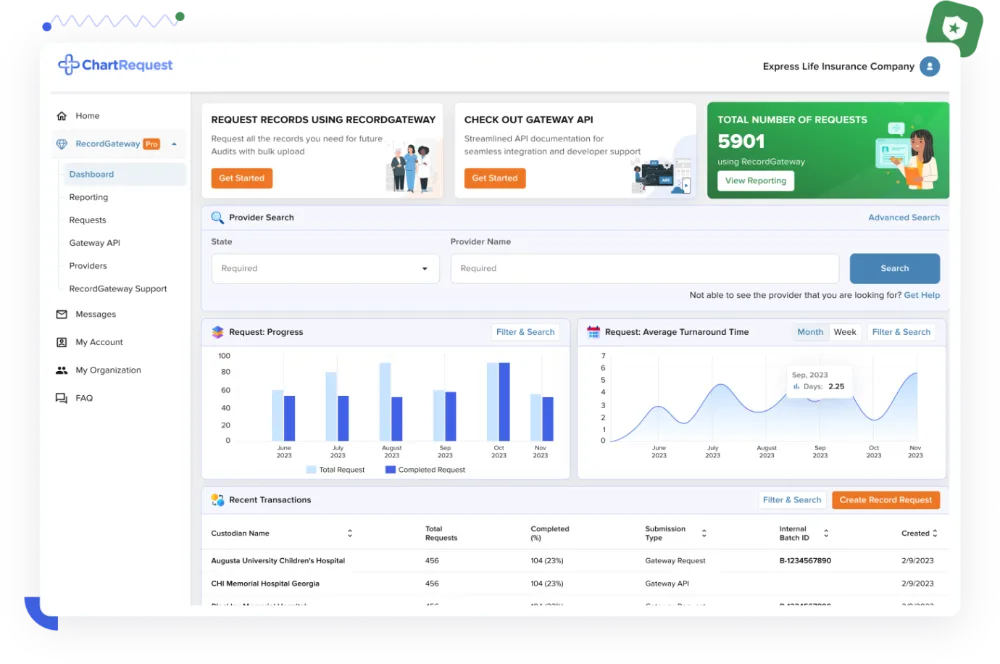
Insurance Companies
During audit season, your insurance company can’t be kept waiting on medical records. Trust the retrieval experts with over a decade of experience to get the records you need quickly and efficiently.
RecordGateway simplifies record retrieval for payors by:
- Access real-time status updates to monitor progress for large requests,
- Get records with uniform naming conventions that fit your needs,
- Maximize retrieval customization with our RecordGateway API.

Patients and Families
ChartRequest Store & Share empowers patients with:
- Real-time status updates available online 24/7,
- Unlimited storage of retrieved records,
- Instant record sharing with healthcare providers.
Schedule a Personalized Consultation for Our Medical Record Exchange Solutions
- One-Stop Shop For Records From Any U.S. Provider
- Industry-Leading Speed and Follow-Up Protocols
- Centralized Dashboard to Organize Your Requests
- Real-Time Status Updates and Comprehensive Reports
- White-Glove Support for Providers and Requestors
- Purpose-Built Systems Based on User Type
- and Much More!

